Guest post originally published on the Sysdig blog by Loris Degioanni, CTO and Founder of Sysdig
Today, I’m excited to announce the contribution of the sysdig kernel module, eBPF probe, and libraries to the Cloud Native Computing Foundation. The source code of these components will move into the Falco organization and be hosted in the falcosecurity github repository.
These components are at the base of Falco, the CNCF tool for runtime security and de facto standard for threat detection in the cloud. They are also at the base of sysdig, the broadly adopted Open Source tool for container forensics and incident response.
This move is an important milestone. It means that from now on, all of the core components of the Falco stack will be part of the CNCF.
What is this exactly?
Let’s start with a diagram showing the main components at the base of Falco and Open Source sysdig:
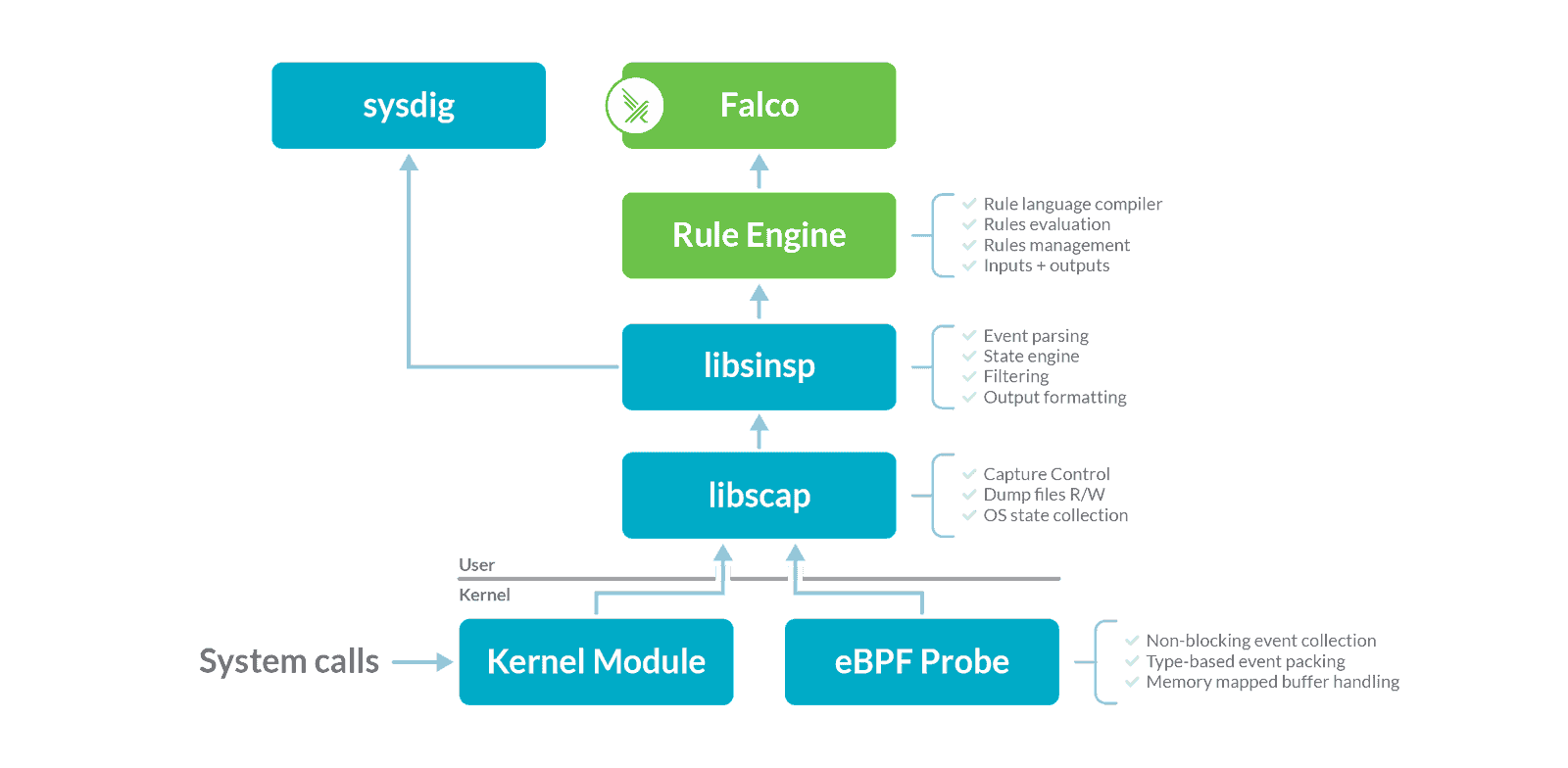
Falco and sysdig operate on top of the same data source: system calls. This data source is collected using either a kernel module or an eBPF probe. The two methods are equivalent in functionality, but the kernel module is a tiny bit more efficient, while the eBPF approach is safer and more modern.
Before being consumed by sysdig or Falco, the collected data needs to be enriched (i.e., a file descriptor number needs to be converted into a file name or an IP address). This is accomplished by two libraries, libsinsp and libscap.
The green boxes in the diagram above identify what was previously owned by the Cloud Native Computing Foundation. This includes the components that make Falco work, but not the ones that collect data. The reason for this separation is that the data collection modules were originally developed for sysdig and they stayed in its repository, while Falco (and other tools) treated them as external dependencies.
As a consequence of this donation, the diagram is changing this way:
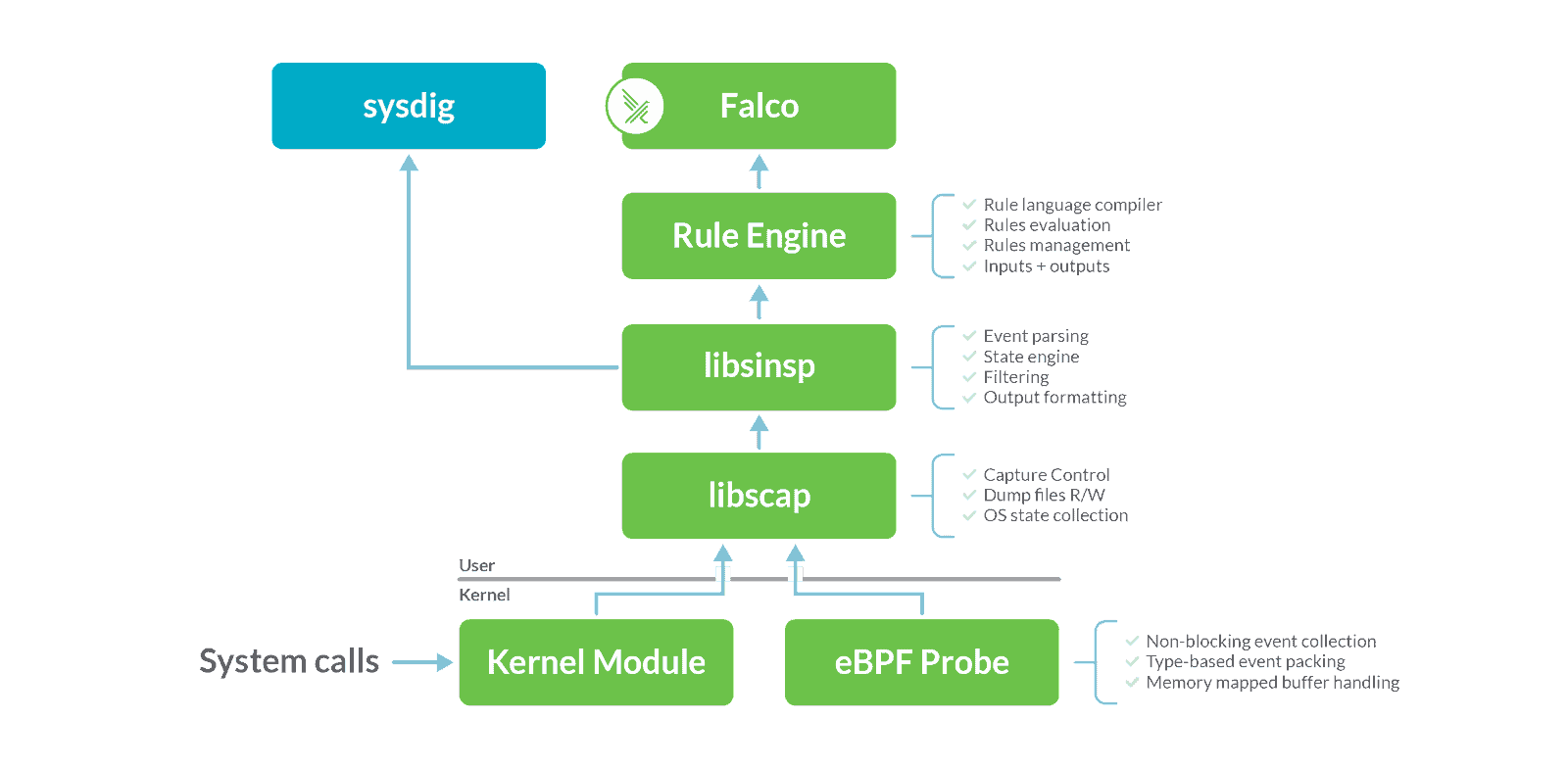
libsinsp, libscap, the kernel module, and the eBPF probe have been relicensed and are now owned by the CNCF. They will live in an independent repository under the falcosecurity organization, and their licensing and governance will be guided by the CNCF community principles.
Why is this important?
Sysdig has been committed to Open Source since its inception and strongly believes the future of security is open. The core technologies behind our products have been available as Open Source software from day one. Today, we’re taking another major step toward ensuring that we live by our principles. In particular, we want to make sure that Falco is fully free and owned by the community.
This contribution completes the effort. It took a bit of time (Falco joined the CNCF in Oct. 2018) because it involved separating the components that were originally part of sysdig and making them independent.
What makes me really excited is that we are taking a set of extremely powerful building blocks and we’re putting them in the hands of the Cloud Native community. Among other things, we are talking about:
- What is likely the most ambitious and sophisticated eBPF script on the planet, safely implementing a sophisticated and extremely efficient system call capture framework in the Linux kernel
- A system call capture library with full support for capture file abstraction.
- A battle tested, 70K+ lines of code kernel event enrichment library.
These components are the perfect foundation for tools in runtime security, troubleshooting, incident response, forensics, and many other areas. I am convinced that the community will embrace them and will come up with some really cool tools on top of them. I, myself, have some interesting ideas that I want to show to the community soon. 😉
Read Leonardo Di Donato and Leonardo Grasso’s take. As two maintainers of Falco, they feel that the contribution will not only help Falco users but also other projects to have a more secure Cloud Native environment.
How can you hack with this?
If you would like to find out more and hack on Falco:
- Get started in Falco.org.
- Check out the Falco project in GitHub.
- Get involved with the Falco community.
- Meet the maintainers on the Falco Slack.
- Follow @falco_org on Twitter.
I hope you will have as much fun using it as we had building it.
And remember: PRs are welcome!