Guest post originally published on Snapt’s blog by Iwan Price-Evans
The software and web industries speak a lot about security and the ability to handle security threats intelligently. In a landscape where security is becoming increasingly complex in nature, it’s important that those running websites, applications, and APIs in production have visibility of the threats their organizations are facing and how best to mitigate those threats.
Threat intelligence can help achieve this, but how does it work and how should security teams integrate a threat intelligence solution into their toolchain?
What Is Threat Intelligence?
Firstly though, it’s perhaps best to unpack what threat intelligence is and how it impacts you.
Threat intelligence is the collection, processing, analysis, and dissemination of current and predictive security data that allows security teams, developers, and automated tools to make intelligent decisions to safeguard the security of their infrastructure, data, and users.
This security Information is increasingly important – not only in the fight against active security threats but also in the defense of an organization’s financial security given the impact that compromised data and core infrastructure will have on reputation and the bottom line.
Solutions that package threat intelligence into a smart platform that integrates with security automation tools, developer pipelines, and incident response workflows can help organizations to understand the threat landscape and to counter threats when – or before – they arise.
The Four Steps To Threat Intelligence
Identifying and communicating security threats in a complex global system is not an easy task. To grasp the value of solutions that automate and simplify this process, it’s important to understand the different steps that go into producing successful threat intelligence.

1. Collection
Threat intelligence starts with raw data: the more, the better. Threat data must be collected from a wide range of sources, including internal and external logs, public or open-source information, and proprietary data from first or third parties.
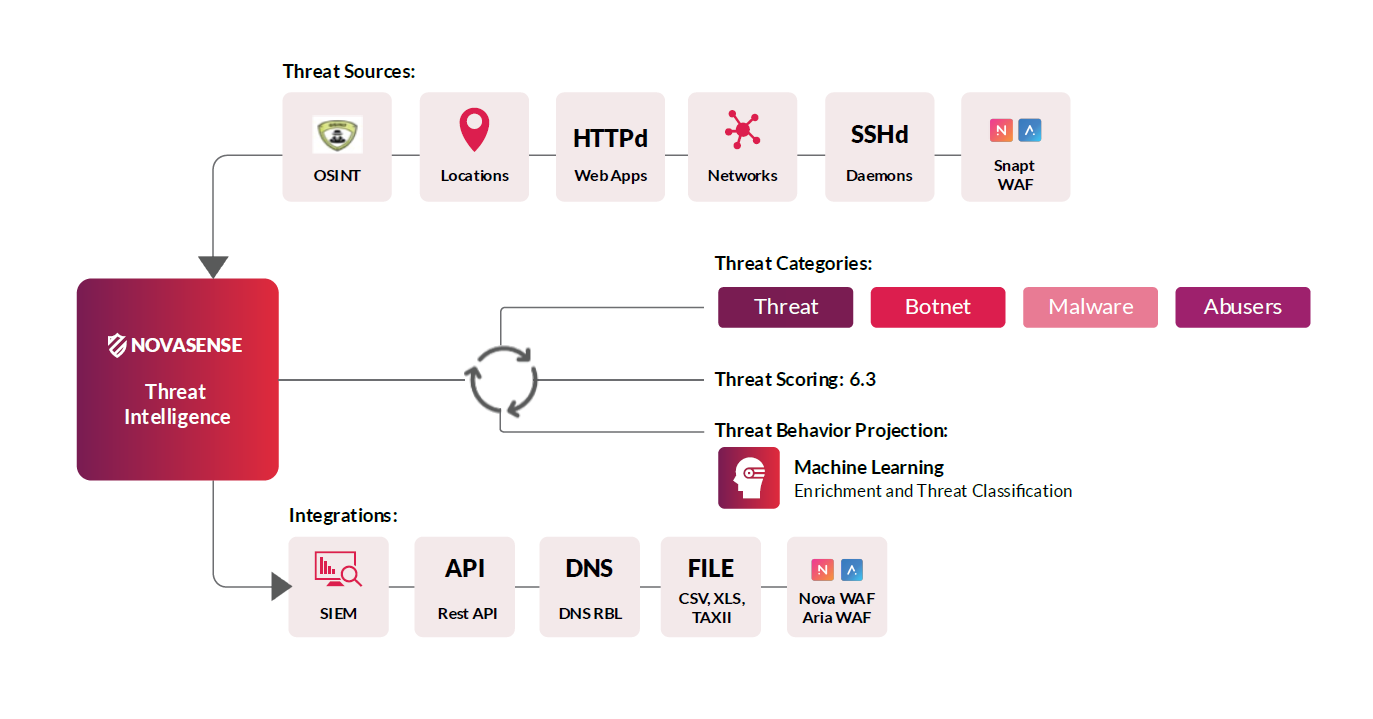
For example, Snapt’s NovaSense threat intelligence platform uses unique threat data sourced from Snapt’s own web application firewalls used in live environments around the world.
Useful threat data includes IP addresses, domains, and file hashes, but it can also include vulnerability information, such as the personally identifiable information of customers, raw code from paste sites, and text from news sources or social media.
This information represents a collection of technical and non-technical information, as well as general information and company-specific data.
The diverse threat data must be collected into a centralized repository for processing.
2. Processing
As all the raw data is collected, it must be processed continually to make it more readable for analysis.
Processing includes sorting, organizing with metadata tags, and filtering out redundant information or false positives and false negatives.
What matters most in this phase though is the ability to process data quickly and reliably to ensure information and analysis can be made available quickly.
The volume and complexity of threats encountered by large organizations produce millions of lines of data every day. A timely analysis depends on the simplification and acceleration of the data processing step.
3. Analysis
Threat intelligence serves many different audiences in any organization, from development teams designing resilient software, to network and system administrators configuring application firewalls, to platform abuse response teams tasked with removing abusive hosts. The analysis step must produce a variety of analyses to meet the needs of each audience.
For example:
- development teams benefit from analyses showing emerging threat trends targeting their industries or the operating systems their applications run on;
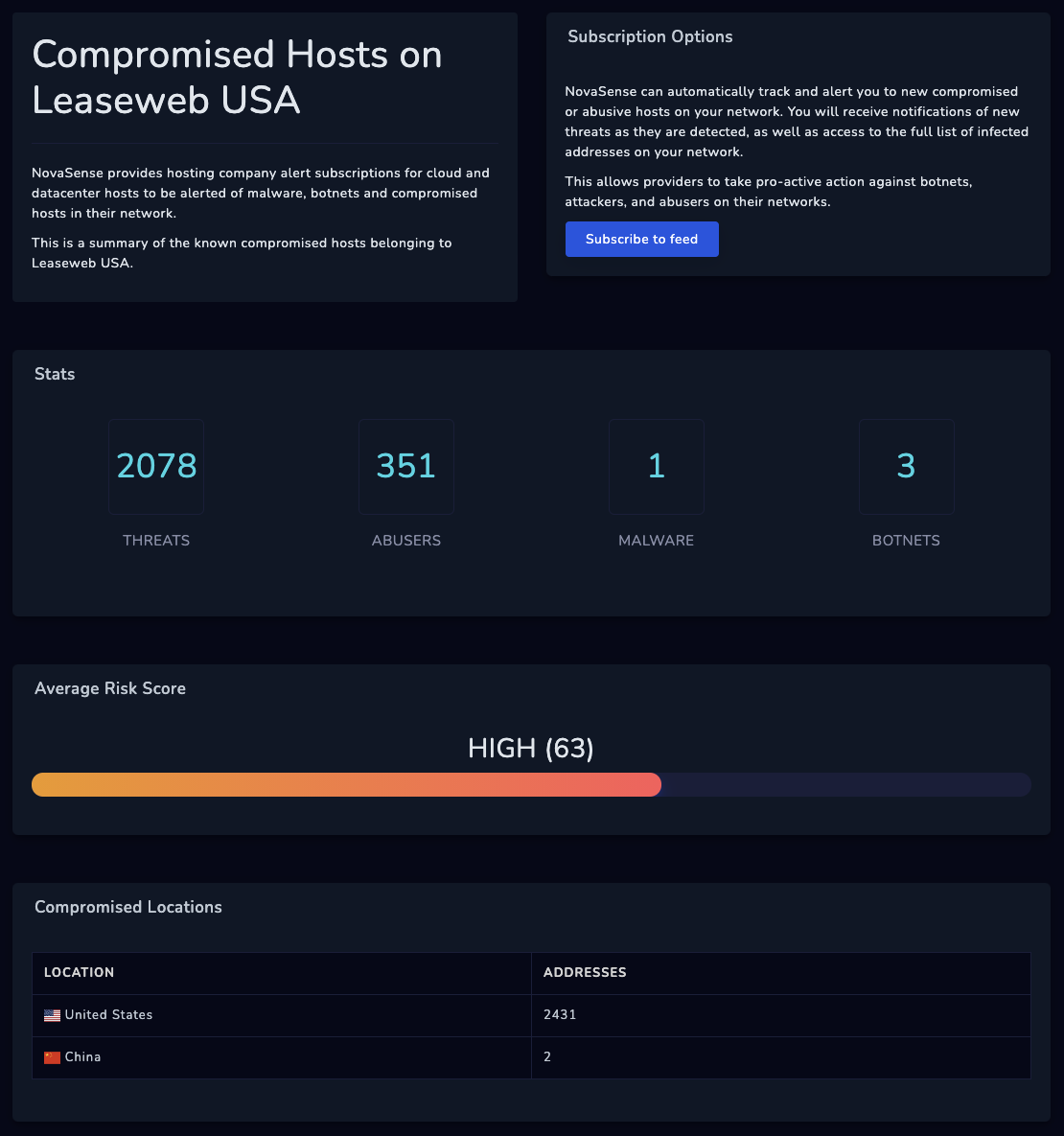
- network and system administrators benefit from analyses identifying active threats by IP address and risk, for automated block-listing;
- platform abuse response teams benefit from analyses identifying abusive hosts using their platform infrastructure, tagged by abuse type (eg. malware, spam, cybercrime, botnet).
Analyzing threat data requires high-performance pattern recognition, triage, and predictive analysis. As a result, threat intelligence solutions benefit enormously from the application of machine learning to their analysis.
4. Dissemination
Threat intelligence is only useful if it is distributed and acted on. In other words, it has to get to the right people or systems, at the right time, and in a way that they can understand and use.
This begins with identifying the right recipients of threat intelligence. Who needs to know? Which systems need to be integrated? For example, an organization might identify its web application firewalls (WAFs) or security incident and event management (SIEM) platform as the desired recipient, to automate their security response and pre-emptively block known threats.
Next, determine the frequency or latency of updates. Which systems need real-time data, and which need daily or weekly updates? Depending on the threat intelligence solution you use, you might not have access to real-time data, and you will have to consider how to factor a delay into your security procedures.
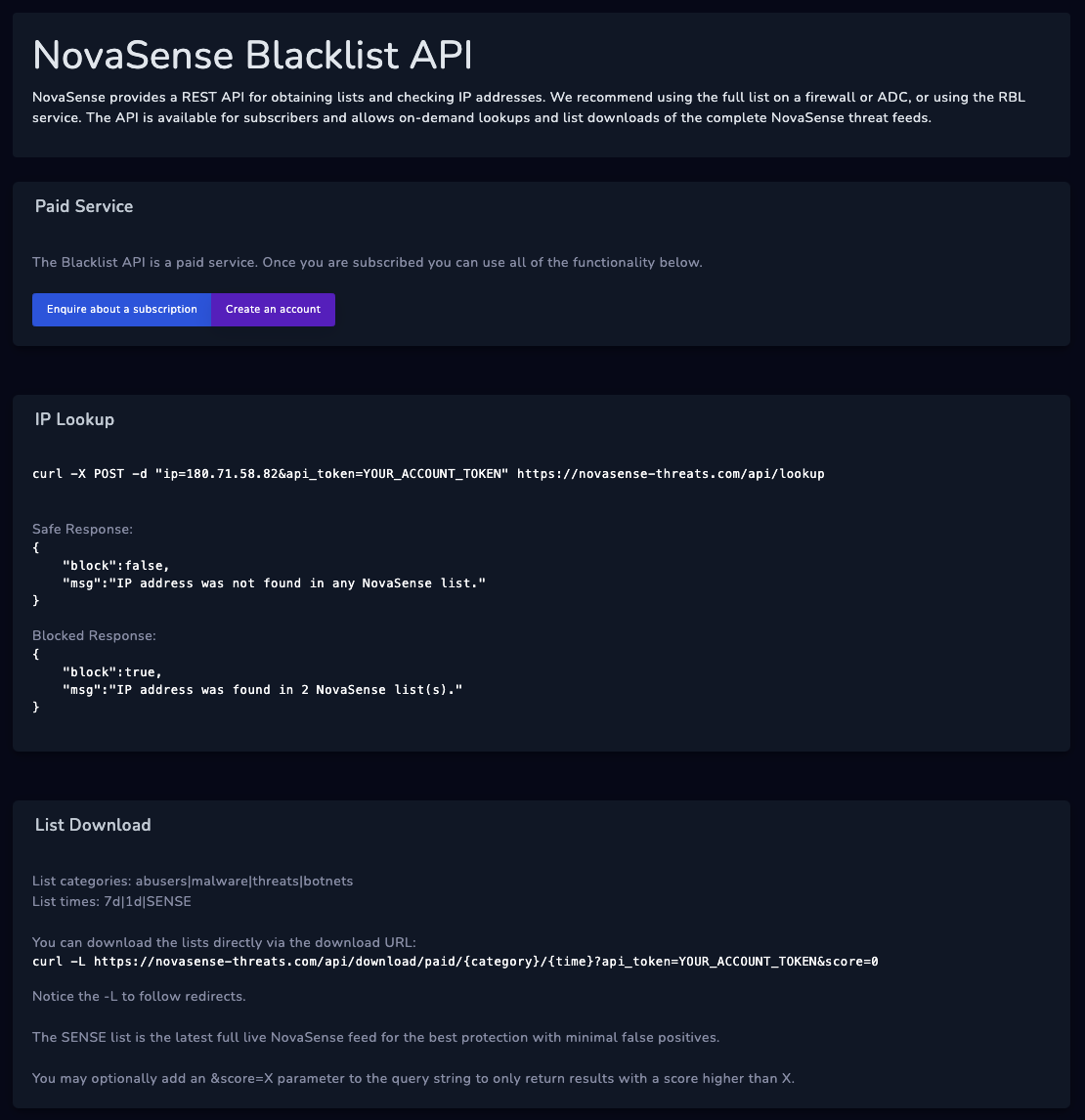
Then, consider the appropriate format for each audience or system. Integrated systems might perform best when syncing data via API – however, you will have to check whether your threat intelligence solution provides comprehensive data over API or has limits on API calls. Sandboxed systems unable to use an API might need data transferred in portable files (eg. CSV files). Human audiences might need visualized threat reports.
Finally, how will threat intelligence fit into the big picture? Every organization ought to add observability to their application pipeline; threat intelligence, when available, should be a part of this.
Three Types Of Threat Intelligence
So we know what that intelligence is and how it all works, but there are different types of threat intelligence that each serve different purposes to an organization.
Strategic Threat Intelligence
Broader trends typically meant for a non-technical audience.
Good strategic intelligence should provide insight into areas like the risks associated with certain lines of action, broad patterns in threat actor tactics and targets, and geopolitical events and trends, often formed on knowing upcoming issues and industry best practices, focusing on the long-term bigger security picture of an organization.
This intelligence may be considered non-technical, but is very important in connecting the needs of the border organization across multiple departments and should be in a language that can be easily executed and followed across all management structures.
Tactical Threat Intelligence
Outlines of the tactics, techniques, and procedures of threat actors for a more technical audience.
It should help security personnel understand, in specific terms, how their organization might be attacked and the best ways to defend against or mitigate those attacks.
It usually includes technical context and is used by personnel directly involved in the defense of an organization, such as system architects, administrators, and security staff.
Operational Threat Intelligence
Technical details about specific attacks and campaigns.
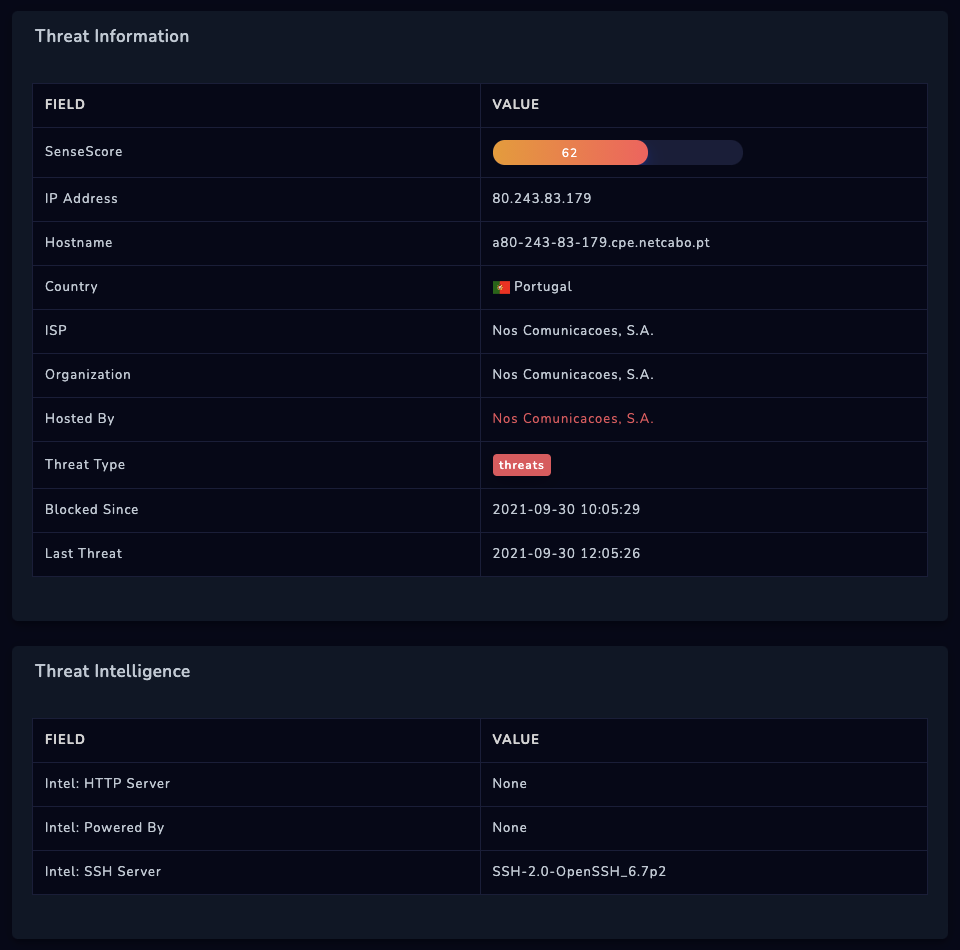
These reports are generally very technical in nature and include information like what attack vector is being used, what vulnerabilities are being exploited, or what command and control domains are being employed.
A common source of technical information is threat data feeds, which usually focus on a single type of indicator, like malware hashes or suspicious domains.
These reports will also provide a company with specifics on the communication and data traveling through an organization and perhaps also identify particular communication patterns which could be of concern and therefore actionable by the security team.
For more information, read about the different use cases for threat intelligence.
Summary
Having threat intelligence integrated into your network is an incredibly important aspect of providing proactive security and ensuring your organization is kept safe from all existing and potential threats.
To give your organization the most robust security posture, look at solutions like NovaSense to provide the real-time, real-world threat intelligence you need.