Guest post by Deepfactor
Given the scalability and flexibility of containers, developers are being encouraged to develop net-new applications—and refactor existing workloads—for Kubernetes. However, the focus on rapid development and deployment presents many security challenges for organizations to manage as they navigate the transition to cloud native applications. The further adoption and maturity of cloud native security practices will continue to have immense impact on organizations undergoing application modernization.
Though cloud native applications still require development, distribution, deployment, and runtime operations, the new paradigm dictates by which these security objectives are efficiently achieved. According to the Cloud Native Security Whitepaper, “In these fast changing environments, prone to rapid iteration, automation in line with the development pipeline is required for secure outcomes. By integrating security as early as possible throughout the development lifecycle, or even earlier with interactive developer training, security organizations can enable preventative security rather than reactive security.”
How to Begin
By understanding the “breadth” of the attack surface evident in cloud native applications, organizations can prepare to adequately detect, mitigate, and manage application security risks in Kubernetes. The following is a diagram generated by Deepfactor showing many of the vulnerable components in Kubernetes applications:
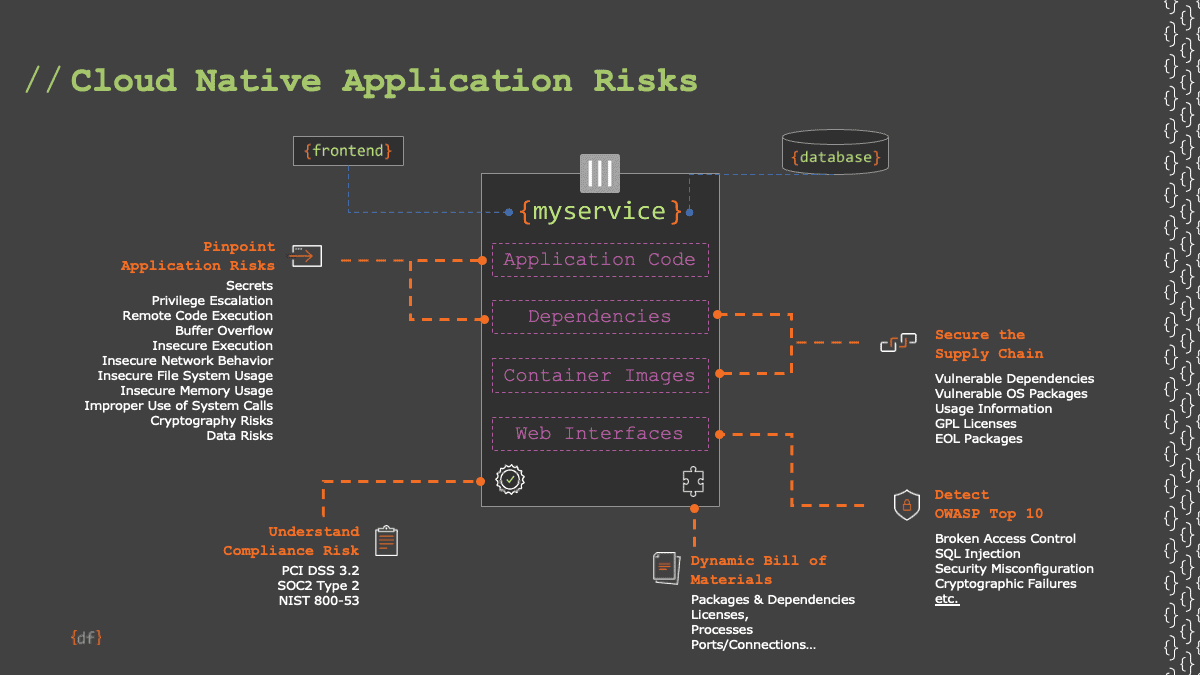
Kubernetes Vulnerable Components
Because of this expansive attack surface, there’s tremendous opportunity in ensuring security is injected throughout software development, rather than “book-ending” the lifecycle with traditional/legacy tools and processes. Instead of “shifting traditional, heavyweight application security tools and processes onto developers, realizing the full advantages of securing applications in development requires purposeful planning for evolving beyond the current, time-consuming checkpoints offered with legacy platforms.” This includes understanding in which stage of Kubernetes development various attack vectors are exploitable:
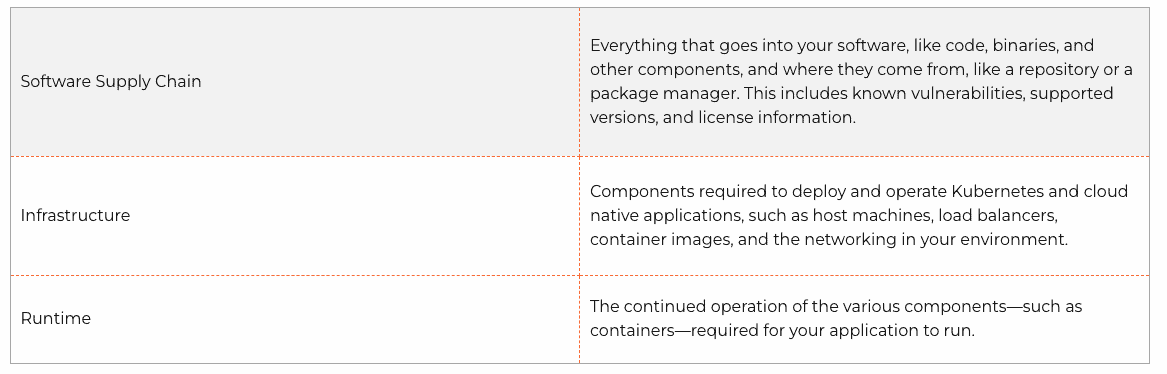
Deepfactor has partnered with DZone and Yitaek Hwang to publish the Kubernetes Security Essentials Whitepaper to further explain each category, and to help developers secure cloud native applications. Though Deepfactor is primarily focused on providing developers with integrated insights spanning application code, dependencies, container images, web interfaces and compliance, the entire software supply chain — from the application code to the deployed containers as well as the Kubernetes cluster — must be secured.