The CNCF Technical Oversight Committee (TOC) has voted to accept cert-manager as a CNCF incubating project.
cert-manager is a Kubernetes add-on to automate the management and issuance of TLS certificates from various issuing sources, for cloud native Kubernetes or OpenShift environments. It will continuously ensure that certificates are valid and up-to-date, and attempt to renew certificates at an appropriate time before expiry. This machine identity is essential to allowing highly secure, encrypted data communications using TLS.
As cloud native environments are highly distributed with high levels of automation, cert-manager has become very popular with developers as an open source tool to protect cloud native workloads with TLS encryption and provide critical security for clusters.
cert-manager also aligns with many other CNCF projects, including Cilium, Knative, SPIRE, Isitio, and Linkerd.
“We are humbled by the trust and support from our users and the community. We are equally humbled by the support and endorsement from the CNCF and believe that reaching incubation status is an important milestone for the project. The cert-manager maintainers look forward to collaborating with the CNCF in our goals to make trust and certificate management more accessible in the cloud native landscape.” – Joakim Ahrlin, Engineering Team Lead at Jetstack, a Venafi company, and cert-manager maintainer.
“cert-manager is probably one of the first applications you install on a Kubernetes cluster. The cert-manager maintainers aim to make this first experience as smooth as possible, while supporting the advanced use cases through our accompanying components, like csi-driver and approver-policy.” – Tim Ramlot, Software Engineer at Jetstack and cert-manager maintainer.
“cert-manager is the de facto standard for X.509 certificates in Kubernetes environments,” said Ricardo Torres, Chief Engineer of Open Source & Cloud Native at The Boeing Company. “Thanks to cert-manager’s flexibility, development teams can leverage the same tool with self-signed certificates in development environments and with certificates signed by trusted CAs in production environments.”
“Dealing with certificates is a task that most cloud native deployments need to handle and not one that should be taken lightly,” said Ricardo Rocha, Computing Engineer at CERN and TOC sponsor for cert-manager. “The popularity and very large user base of cert-manager shows it has gained the trust from the users and has become an integral part of the ecosystem. With the project moving to incubation, I look forward to watching the community continue growing and seeing the project integrate further with other cloud native tools.”
Main Components:
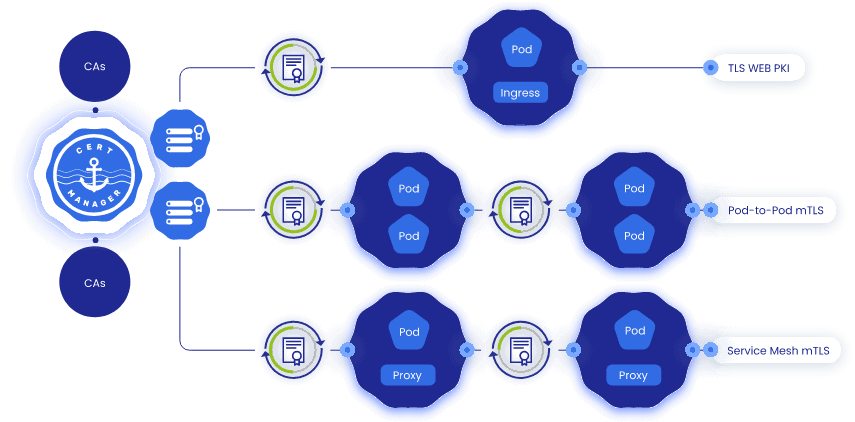
- cert-manager controller: which lets the user create Certificates backed by K8s Secrets containing the keys for your certificates. It also allows you to directly create these Secrets for Ingress resources.
- csi-driver: cert-manager includes a CSI driver library that enables users to easily build opinionated CSI drivers that deliver certificate key pairs to Pods in Kubernetes. cert-manager also has several implemented CSI drivers such as csi-driver-spiffe, as well as the generic csi-driver.
- Issuers: cert-manager has a number of issuer integrations with third party certificate providers, including LetsEncrypt, Amazon Route53 and Venafi.
- Approval API: The approval API is a mechanism in cert-manager to approve or deny certificate requests. Decisions on this API can be automated, like in the case of approver-policy, a CRD based policy controller.
- trust-manager: As part of the team’s initiative to improve trust distribution in Kubernetes, trust-manager is an early project intended to help users distribute CA bundles across their clusters.
Notable Milestones:
- 9.4k GitHub Stars
- 2057 merged pull requests
- 2531 closed issues
- 300+ contributors
- 136 Releases
- 7k Slack members
“The cert-manager project is a fantastic work of engineering that lowers the barrier of obtaining security certificates for the Kubernetes and cloud native ecosystem. We look forward to supporting the growing community and increasing the number of adopters,” said Chris Aniszczyk, CTO of The Cloud Native Computing Foundation.
cert-manager is continuously adding support of upstream Kubernetes enhancements, including Gateway API, CSR API and Trust Anchor Sets and has made significant progress since joining the CNCF Sandbox in 2020 including:
- istio-csr enables users to use cert-manager to issue certificates for istiod and sidecars
- Introduced the cert-manager security policy with vulnerability reporting instructions
- cert-manager was sandboxed at v1.0, and since then we’ve made 10 minor version releases, to v1.10
- Added experimental cert-manager support for Kubernetes Gateway API
- Migrated cert-manager from sponsoring GitHub organisation to cert-managers own
- Participated in Google Summer of Code with a project to simplify installation of cert-manager
- Supply chain security: adding signatures for containers and helm charts
- Launched a refresh of the website on 2022-04-13, https://cert-manager.io/
- Number of maintainers has grown from 3 to 9
- Downloads of cert-manager images was at around 2M when sandboxed and has been slowly declining to ~1.7M to date – but we believe it has do with image caching and docker hubs pricing model change
- User research which gave the project a 99% approval rating
- The visitors to docs website has doubled since sandboxing, from average 1000 daily website visitors to 2000, a better signal for adoption rate than image downloads.
The team is also improving the extensibility and user + developer experience of cert-manager and aiming to shrink the core of cert-manager to reduce deployment complexity, binary size, attack surface and image sizes.
Further information about the roadmap can be found here.
As a CNCF-hosted project, cert-manager is part of a neutral foundation aligned with its technical interests, as well as the larger Linux Foundation, which provides governance, marketing support, and community outreach. For more information on maturity requirements for each level, please visit the CNCF Graduation Criteria.