Guest post by Edgeless Systems
Constellation is the first always-encrypted Kubernetes, released as open source in September. It’s a K8s distribution like SUSE Rancher or RedHat OpenShift.
What makes Constellation special is that it leverages confidential computing technology to shield entire clusters and all workloads from cloud infrastructure. From the inside, it’s a fully-featured, CNCF-certified K8s engine. From the outside, it’s 100% confidential.
We designed Constellation with two objectives in mind:
- It should provide the best possible security and essentially allow one to run a K8s cluster on potentially compromised infrastructure safely. Even privileged cloud provider employees shouldn’t be able to access the data in a cluster.
- From a UX perspective, it should work like normal K8s.
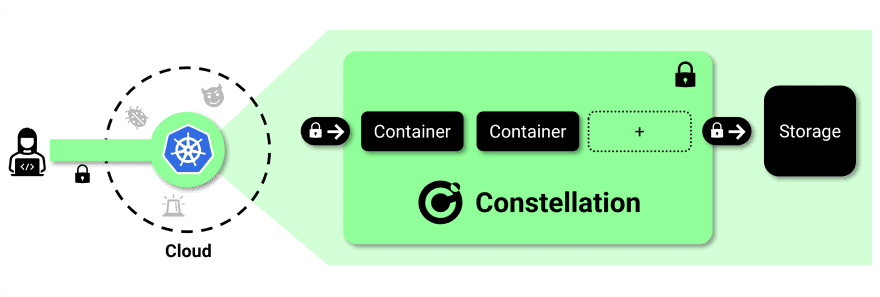
How it works
The key ingredients are AMD SEV-based Confidential VMs (CVMs), which are available in Azure and GCP. CVMs protect workloads against a compromised host and malicious admins. For this, CVMs remain encrypted at runtime in memory, are strongly isolated, and have advanced remote attestation capabilities. Intel and Arm have announced similar features for their server CPUs, and we plan to support these once they become available.
Instead of protecting individual workloads, we have put the entire K8s nodes inside CVMs so that any workload that runs inside these VMs is automatically runtime encrypted. That also includes the control-plane nodes. Thereby protecting the confidentiality and integrity of the cluster’s control plane, state, and workload configuration.
Architecture & features
Constellation consists of three main components: a CLI, a custom node image, and a set of services.
The CLI allows for the easy setup of a Constellation cluster. For example:
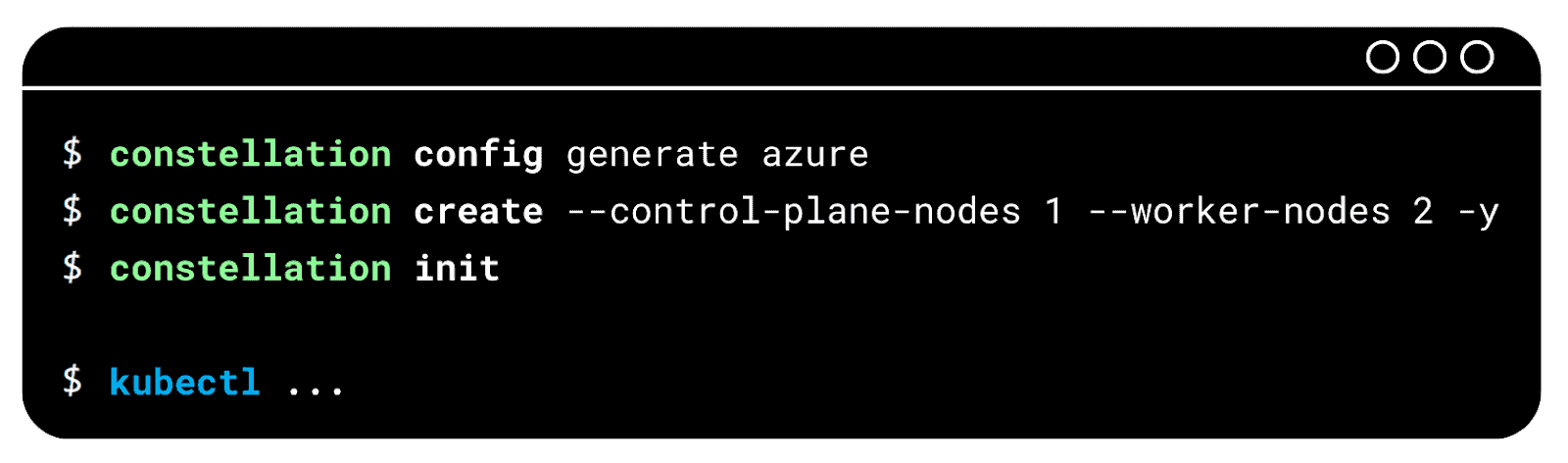
The CLI automatically creates CVM-based nodes using Constellation’s node image. The node image is based on Systemd’s mkosi for bespoke OS images, optimized for CVM remote attestation and containerized workloads.
Internally the CLI utilizes terraform for infrastructure provisioning, and we’re working on a terraform provider to replace the CLI entirely for integrations with IaC and GitOps pipelines.
Cluster attestation/verification
The first node in a cluster is verified by the CLI directly. After that, all others are verified by existing nodes. Thus, transitively, the users know that only “good” nodes running “good” images are part of the cluster.
How to know what a “good” node image is? Easy. We sign all node images (and the CLI) and publish the corresponding signatures on the Sigstore’s public transparency log.
Network & cloud storage encryption
After a node is verified, it receives cryptographic keys to talk securely to other nodes over the network and to encrypt data that is written to cloud storage. These keys are all managed by Constellation. For maximum control over keys, Constellation can be used with an external KMS via KMIP. For network encryption, Constellation relies on Cilium.
CVM runtime encryption, network encryption, and storage encryption together ensure that all data is always encrypted.
Check the README for a more comprehensive list of features and benchmark comparisons.
What is it good for
Always-encrypted and isolated K8s clusters have many exciting use cases. Here are a couple of them:
- Increase the security of your clusters and prevent data breaches
- Increase the competitiveness of your SaaS offerings – Provide your customers with provable guarantees of where their data can be accessed and by whom
- Meet regulatory requirements (GDPR, HIPAA)
- Move sensitive workloads from on-prem to the cloud
Conclusion
Companies are aggressively moving to ‘cloud first’ and ‘cloud only’ strategies for application deployment. Simultaneously, regulators and legislators are increasing the requirements on organizations to protect the data they manage. Constellation is the first always-encrypted Kubernetes distribution. It provides you with the easiest and safest way to protect your data in all states of its modalities: at rest, in transit, and during use; from operators of the infrastructure, from malware, and from other customers running on the same infrastructures. Join us in our pursuit to create a future where companies and people retain control over their data, no matter where it is, in any application. Try Constellation for free. It’s open-source and on GitHub, feel free to leave us a star or contact us on Discord.