Guest post originally published on SighUP’s blog by Simone Ragonesi
We will introduce you to the powerful combination of Open Policy Agent (OPA) and Gatekeeper for Kubernetes security.
In this article, we will introduce you to the powerful combination of Open Policy Agent (OPA) and Gatekeeper for Kubernetes security.
OPA serves as a versatile policy engine, while Gatekeeper, an admission controller, extends OPA’s capabilities to enforce policies in real-time during resource creation and updates.

As the adoption of Kubernetes continues to grow, ensuring robust security within these dynamic container orchestration environments becomes increasingly vital.
Kubernetes provides a powerful platform for deploying and managing containerized applications, but it also introduces unique challenges related to configuration management, access control, and compliance.
To address these challenges, Open Policy Agent (OPA) and its Gatekeeper extension have emerged as indispensable tools for enforcing policies and bolstering Kubernetes security.
What is Open Policy Agent (OPA)?
Open Policy Agent (OPA) is an open-source, general-purpose policy engine that allows you to define, manage, and enforce policies consistently across various parts of your technological stack.
OPA uses a declarative and non-turing-complete policy language called Rego, which makes it easy to express complex policies in a human-readable format.
Its versatility enables it to be used in a wide range of applications, from microservices authorization to cloud security and, notably, Kubernetes policy enforcement.
This flexibility, expressed through Rego, makes OPA an exceptional tool when it comes to generating custom and tailored rules based on specific business logics, requirements and regulations.
Introducing Gatekeeper for Kubernetes
Gatekeeper is a Kubernetes-native admission controller that extends the capabilities of OPA to Kubernetes clusters.
By combining OPA’s policy engine with Kubernetes’ admission control mechanism, Gatekeeper enforces policies on Kubernetes resources during creation and update operations.
This provides organizations with a powerful way to validate and enforce desired configurations, security best practices, and compliance requirements automatically.
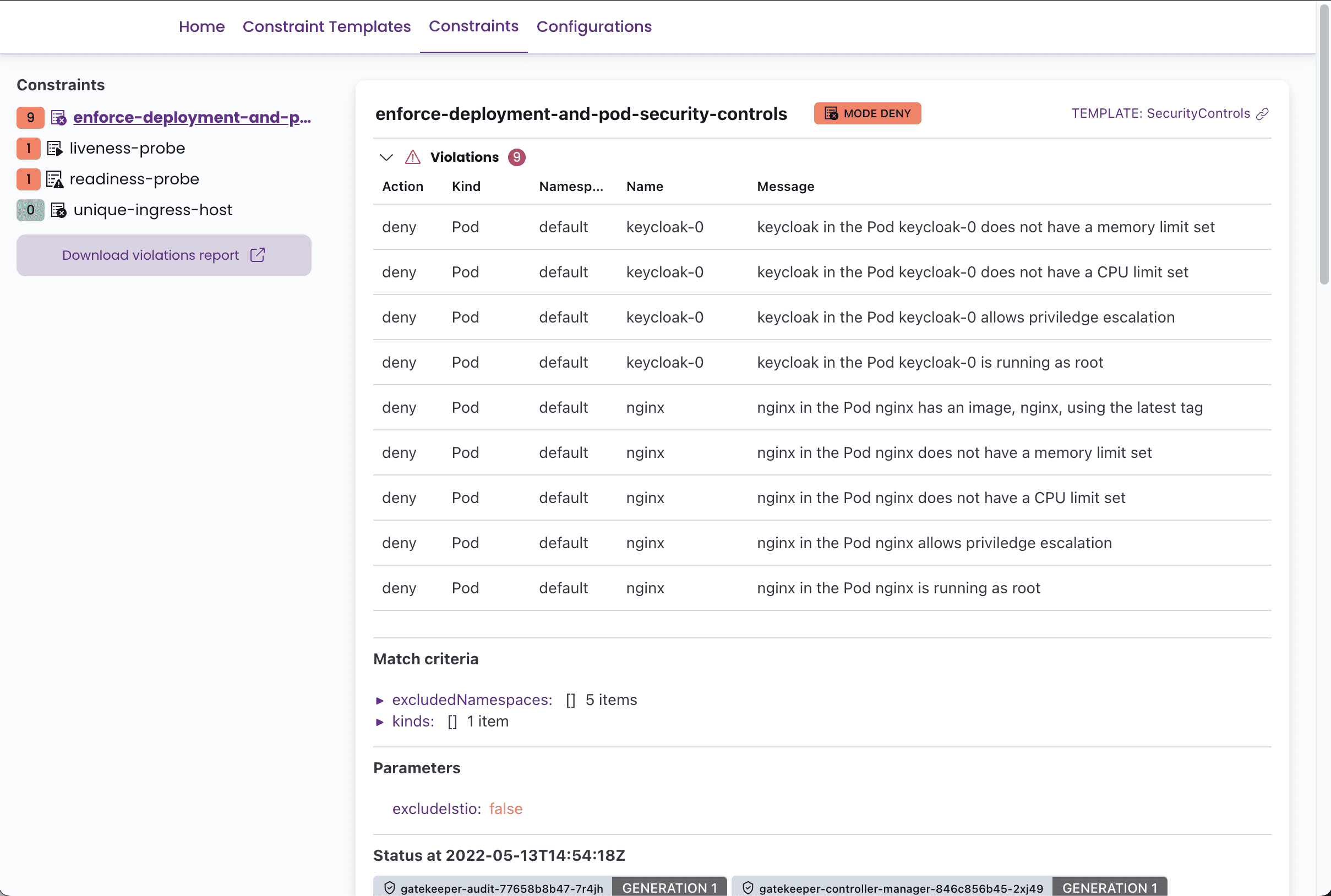
It is worth noting that SIGHUP has developed an open-source tool called Gatekeeper Policy Manager. This tool provides a simple read-only web UI designed to assist cluster administrators in viewing the status of OPA Gatekeeper policies within a Kubernetes Cluster.
Key Benefits of Using Gatekeeper
Policy Enforcement: Gatekeeper enables organizations to define custom policies that match their specific security requirements.
This includes validating resource configurations, checking for compliance with regulatory standards, and enforcing best practices.
Real-time Control: With Gatekeeper acting as an admission controller, policies are evaluated in real-time, preventing the deployment of resources that violate security guidelines.
This immediate feedback loop enhances the security posture of the Kubernetes cluster.
Uniformity and Consistency: Gatekeeper ensures uniformity and consistency in resource configurations by applying policies across all namespaces and clusters. This helps prevent misconfigurations and reduces the risk of security incidents.
Flexibility: OPA’s Rego language provides a flexible and expressive way to author policies.
This allows organizations to adapt policies to their unique use cases and security requirements, providing greater control over their Kubernetes environment.
Common Use Cases for Gatekeeper Policies
Pod Security Policies: Gatekeeper can enforce specific pod security policies, such as requiring the use of specific security context constraints or blocking privileged containers.
Namespace Quotas: Organizations can define policies to enforce resource quotas on namespaces, preventing resource abuse and ensuring fair allocation.
Network Policies: Gatekeeper can enforce network policies to control pod-to-pod communication, restricting access based on defined rules.
Custom Business Rules: Gatekeeper allows organizations to define custom policies that align with their specific security, compliance, and operational needs.
Practical Example
In order to demonstrate the flexibility of OPA Gatekeeper, we will now introduce a practical use case.
Please note that this is solely an illustrative example, and careful evaluation should be conducted before deploying it in a production environment.
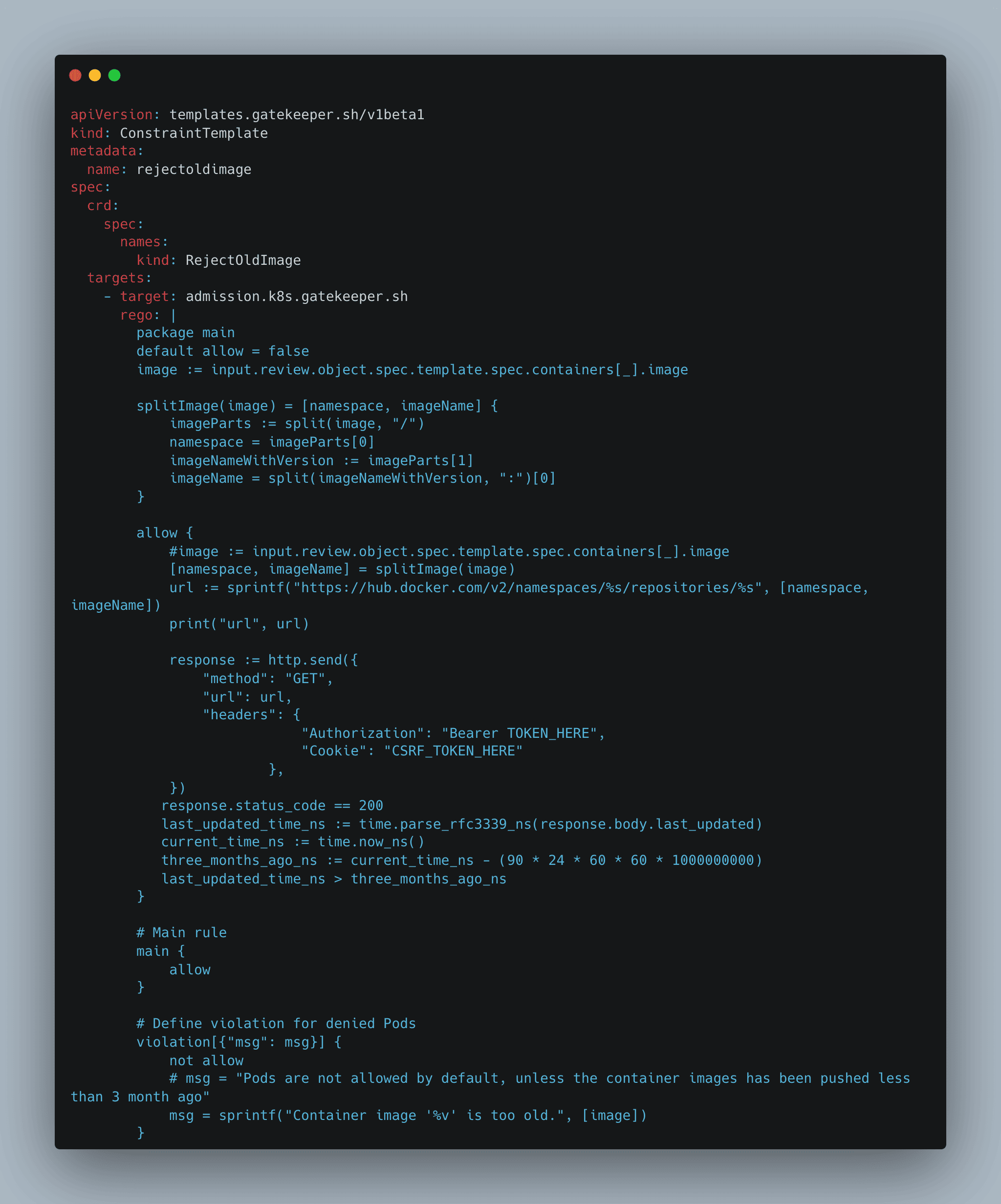
Let’s assume that your company imposes a compliance requirement stating that container images used for the Deployments on your cluster cannot be older than three months; otherwise, the deployment must be rejected.
Kubernetes lacks the ability to determine the last push date of an image before applying the deployment manifest.
Fortunately, Gatekeeper comes to our aid.
Below is the implementation of the ConstraintTemplate CRD with the necessary Rego code to perform this validation (assuming docker hub is the reference registry):
Conclusions
In a Kubernetes environment, maintaining robust security and compliance is crucial for safeguarding applications and data.
Open Policy Agent (OPA) and Gatekeeper offer a powerful approach to enforce policies and strengthen Kubernetes security.
By leveraging OPA’s flexible policy language and Gatekeeper’s admission control capabilities, organizations can confidently mitigate risks, prevent misconfigurations, and ensure compliance with security best practices.
As the Kubernetes ecosystem continues to evolve, adopting OPA and Gatekeeper as integral components of the security strategy will be paramount for maintaining a secure and resilient Kubernetes environment.
With these tools in place, organizations can embrace the full potential of Kubernetes while keeping security at the forefront of their operations.