Member post originally published on Coredge’s blog by the Coredge team

Overview:
The Cloud Auditing Data Federation (CADF) facilitates the federation of normative audit event data to and from cloud providers, which is why it is significant. It offers fresh perspectives on the hardware, software, and network infrastructure of the provider that are used to power certain tenant applications in a multi-vendor setting. Regardless of where applications run, on-premises, in a hybrid cloud, or in a public cloud, compliance with corporate policies and industry laws is a crucial component of every organization’s strategy. By making existing cloud and service audit interfaces, technologies, and tools more consistent, compatible, and even functional, CADF seeks to address significant issues.
Anyone can utilize the full event model defined by the Cloud Auditing Data Federation (CADF) standard to fill in the necessary information to certify, self-manage, and self-audit application security in cloud environments.
Why CADF:
Application security (AppSec) is the practice of identifying and reducing the number of security flaws while reducing the probability of successful assault. It addresses every security issue that comes up during the design, creation, and deployment of an application. CADF offers application security certification, self-management, and self-audit in cloud environments, which can assist customers in ensuring compliance with corporate policies and industry laws.
CADF is crucial and significant for application security as it offers a standard method to capture, share, and analyze audit data in cloud environments. It supports monitoring and confirming the security controls and policies of their apps and resources for cloud providers and users. Following are the ways in which CADF events can help enterprises.
Disaster Recovery: CADF can assist with disaster recovery by offering a consistent and thorough record of the activities that took place before, during, and after a disaster. With the aid of this, the disaster’s cause can be found, its effects can be evaluated, normal activities may be resumed, and similar disasters can be avoided in the future. For instance, CADF can offer information about who, what, when, where, why, and how an incident occurred if a cloud application is subject to a data breach or a denial-of-service attack.
Incident Analysis and Response: By offering a standard format and interface for gathering and requesting audit data from various sources and domains, CADF can aid in incident investigation and response. This can aid in correlating and grouping the events, finding anomalies, gauging their severity, and choosing the best course of action. For instance, CADF can offer measurements and indicators of an event and its effects on the quality of service if a cloud application encounters a performance decrease or configuration error.
Proactively Detecting Anomalous Behavior from Events: By offering a rich collection of attributes and tags that may be used to categorize and filter the events based on different criteria, CADF can assist with proactively detecting aberrant behaviour from events. Applying machine learning and analytics approaches to spot patterns and trends, establishing alerts and notifications, and building customized logs and reports can all benefit from this. For instance, if a cloud service has a potential vulnerability or compliance problem, CADF can offer details about the resources used, the actions taken, the results seen, and the circumstances surrounding the event.
This standard defines a way to attach domain-specific identifiers, event classification values, and tags that can be used to dynamically generate customized logs and reports for cloud subscribers or customers. It also includes a robust query interface that can be extended to reflect the distinct resources of each provider. Furthermore, CADF has the capability of real-time performance metering and monitoring, which may be utilized to guarantee customer quality of service, going beyond log-based monthly audits.
Organizations that employ collaborative web services like Slack, Microsoft Teams, or Box as well as those operating in a multi-cloud environment hosted by a third-party cloud provider like Amazon, Microsoft, or Google must prioritize cloud application security. Any organization’s strategy must include a vital requirement for compliance with internal policies and industry standards. Some other benefits of CADF compliance are:
1- It facilitates cross-vendor information sharing through the creation of its data format and interface, which can assist clients in comparing and evaluating various cloud service providers.
2- Real-time performance metering and monitoring capabilities are provided, enabling users to assess and enhance the level of service provided by their cloud applications.
3- It outlines a method for tagging, classifying, and attaching domain-specific identifiers that can be used to dynamically create tailored logs and reports for cloud subscribers or clients.
Industry Specific Usage:
With the evolution of new-gen cloud-native solutions like 5G, innovative city projects, autonomous vehicles, IoT, and more, the application footprint has been expanding exponentially, leading to the requirement of rolling out and managing deployments over distributed infrastructure spanning from the cloud to private datacenters and edge environments. However, it presents operational challenges, making mini-data centers and edge locations difficult to manage across multiple distributed locations.
Managing multi-cloud and edge clouds from a single control point has become crucial as dispersed cloud environments rise. Enterprises seek methods to orchestrate, automate, and manage their infrastructure resources, focusing on security and privacy.
Proposed solution:
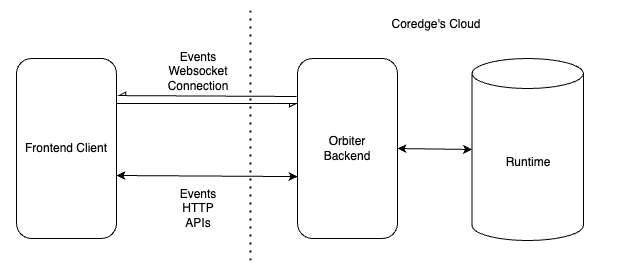
Cloud Orbiter provides a comprehensive solution to help you manage your applications efficiently in cloud and edge environments. Orbiter has designed a solution to record events and expose them to every authorized user in real time. Users can also view older events via a dedicated view of paginated events on the front end.
Cloud Orbiter’s asynchronous and event-driven architecture heavily depends on the runtime database for managing the lifecycle and states of various objects in Orbiter. When the system or the user triggers an operation on a given object, the runtime is updated with state information after all of the asynchronous processing for that object is complete. Cloud Orbiter records these events along with updating state information into the runtime.
Cloud Orbiter by Coredge:
A unified Kubernetes management platform designed for distributed and edge clouds that provides a public cloud experience for edge data centers, enabling centralized operations and automation for distributed Kubernetes clusters. The platform efficiently manages virtual machines, containers, and bare metal across any infrastructure, offering a unified cloud experience for application and infrastructure lifecycle management. Cloud Orbiter caters to diverse service providers, government organizations, and data centers, assisting in various aspects of cloud services, including engineering, delivery management, and maintenance. Connect with our experts to learn more about Cloud Orbiter.