Member post originally published on Fairwinds’s blog by Joe Pelletier
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) continue to update their Kubernetes hardening guidance, making recommendations to help organizations ensure they are hardening their Kubernetes clusters. This strong defense-in-depth approach helps organizations ensure that when an attacker compromises a cluster, the blast radius is as small as possible. At a high level, the guide makes the following recommendations for hardening Kubernetes:
- Scan container images and pods for vulnerabilities and misconfigurations.
- Run containers and pods with the least privileges possible.
- Use technical controls to enforce minimum levels of security.
- Use network separation and hardening to minimize the damage caused by a compromise.
- Use firewalls to limit network connectivity when possible and use encryption to protect confidentiality.
- Use strong authentication and authorization to limit user and administrator access and minimize the attack surface.
- Audit logs so administrators can monitor activity and get alerts to potentially malicious activity.
- Create a security policy that requires the periodical review of all Kubernetes settings and use vulnerability scans.
Are Organizations Applying NSA Hardening Checks?
Fairwinds Insights supports a number of the NSA’s recommendations, adding several additional checks to help organizations align to the NSA guidelines. This year’s Kubernetes Benchmark Report analyzed data from over 330,000 workloads, using data from hundreds of organizations to evaluate alignment with best practices related to cost efficiency, reliability, and security. The latest report also includes a section looking at alignment with the NSA hardening checks specifically.
Linux Hardening
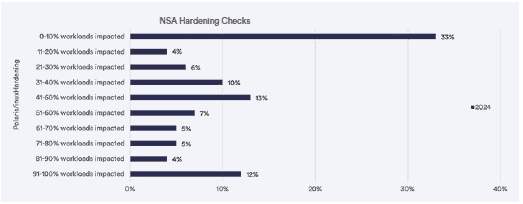
Frequently, workloads have more privileges than needed to run their applications. Tuning the privileges of your containers helps you to minimize the speed and impact of a container compromise. Fairwinds checks whether a workload uses AppArmor, SELinux, Linux Capabilities, or a seccomp profile to grant workloads the minimum privileges needed to function. Minimizing the privileges of a workload also minimizes an attacker’s ability to gain access to other workloads or to your cluster.
In the 2024 Benchmark, analysis showed that 33% of organizations had more than 50% of workloads with excessive privileges allowed. 12% of organizations had only 91-100% of workloads impacted, with the rest distributed in between. This shows that organizations have room for improvement in terms of implementing Linux hardening. They must spend some time identifying these over-privileged workloads to make this change to align to NSA guidelines. Polaris is an open source policy engine for Kubernetes that can help you identify this issue so you can remediate it.
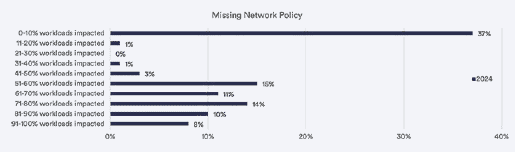
Missing Network Policy
Network Policies in Kubernetes control traffic flow with other Pods, IP addresses, or namespaces.You can use Kubernetes NetworkPolicies for individual applications in your cluster to specify how a pod can communicate with other network entities over the network. If a pod doesn’t have an NetworkPolicy that limits its egress and ingress traffic, it may allow access to external resources or access from other pods that you don’t want to permit.
The Kubernetes Benchmark showed that 37% of organizations have a network policy in place to protect workloads from unwanted traffic. Unfortunately, analysis also showed that 58% of organizations are missing a network policy on 51% or more of their workloads. Setting a network policy is a critical step to securing containers, so it’s surprising that so many organizations do not have this hardening in place. Polaris also includes policies to help identify workloads missing a network policy so you can address those issues.
NSA Hardening Guidance Compliance
As the industry provides additional feedback on hardening Kubernetes environments against malicious attacks and the threat landscape evolves, the NSA and CISA will continue to update the Kubernetes hardening guide. The Kubernetes and cloud native ecosystems are also evolving rapidly, resulting in new solutions and new challenges. Keeping up with these changes is difficult, particularly in complex environments.
Malicious actors are all too ready to take advantage of a leaked kubeconfig, leaked cloud credentials, supply chain vulnerabilities, exposed dashboards, or known security vulnerabilities. All of these avenues of attack could allow an attacker to execute their own code within your cluster, escalate privileges, cover their tracks, and create a persistent foothold. This allows malicious actors to steal secrets and sensitive data, consume your compute resources for their own gain, or otherwise put your business at risk. Without solutions to help you identify workloads with excessive privileges or missing network policies, it’s challenging to find and fix these problems to minimize the potential impact of an attack.
Polaris and Fairwinds Insights are two solutions that can help organizations track the recommendations for hardening Kubernetes clusters and assess whether there are gaps that need to be addressed. As teams deploy more clusters in more environments, it’s important to be able to continuously evaluate security — and alignment with NSA guidance — at scale.