Member post originally published on the ngrok blog by Joel Hans
Developers love a groove.
No, I don’t mean a touch of jazz to class up your workday, but the specific patterns you rely on for building great applications. Think of the grooves in the vinyl you might play for said jazz. Grooves that work, like development environments, version control, declarative configurations, code review with your peers, CI/CD pipelines for your test suites…
By settling into that groove, you get shifted-left security without breaking your brain, more transparency into what everyone is building together, and higher quality. That’s the undeniable advantage of working with these proven traditions. The developer experience for building applications stays relatively strong through production. In the cases where it gets operationally messy, you still have plenty of exciting software delivery and DevSecOps platforms to pick from that will help you get over the finish line.
Taking APIs to production in the same groove is another entirely different matter.
Tip: Too eager to peek at the real infrastructure behind an APIOps workflow with ngrok? Skip down to the Building with ngrok’s production-grade API gateway and unified ingress section.
Most of the entrenched API gateway providers—both those deployed on-premises and in the cloud—leave you hanging right before you deploy to production. When you try to enable must-have policies like JWT-based authentication, you have to trudge your way through the gateway’s awkward web console, where you get the joy of working with languages like CSharpScript. Adding rate limits isn’t much better, with a sequence of curl requests to the admin API.
Even if they do offer a more developer-friendly configuration process, it’s usually an afterthought they’ve tacked on to keep up with the competition. Using it requires a painful rip-and-replace process to get yourself back to feature parity.
These outcomes might be fine if you have a dedicated DevOps or platform engineering team who handles all operational worries on your behalf. Doesn’t that sound nice? The reality is that most developers can’t afford—in time, cognitive load, and risk to quality—to jump grooves at the last possible moment. Abandoning a Git-driven development lifecycle when you need good developer experience can’t be a viable long-term solution.
How much would you benefit from defining API gateway configuration in code, version-controlled traffic policies, and repeatable deployments in any environment?
The origins and applications of APIOps
If you haven’t heard of APIOps, here’s the TL;DR: APIOps aims to integrate the beneficial processes (more grooves) of DevOps and GitOps into API development.
APIOps borrows the automation and integration fundamentals from DevOps to improve your collaboration across the entire API lifecycle, speeding up your release cycle while minimizing bugs. It also folds in what makes GitOps great for automating how you provision infrastructure, like relying on Infrastructure as Code (IaC) and formal change mechanisms, for more manageable and higher-quality production deployments.
Because your Git repository is the canonical source of truth, dictating not just what the upstream service is but how it’s made available in production, you can start to answer that last question:
- Set configurations in code? When you declare how your API gateway should operate using IaC fundamentals, you don’t have to worry about documenting the exact
curlcommands you used against the gateway provider’s API. - Version-control your policies? With Git, you collaborate with peers from a canonical source of truth. Your API—its application code and gateway configurations—is your Git repository and nothing else.
- Deploy in any environment with the same process? Because GitOps (and thus APIOps) configurations define the desired state of your deployment, they repeat the same infrastructure every time you deploy. That could be on your local development environment or your production server.
GitOps and APIOps also gives you access to some other benefits:
- Transparency into the architecture and operation of your deployment, as everything must reside within the same repository.
- A built-in audit log of API configuration and policy changes—just look at your commit history!
- Easier rollbacks via
git revert. - Repeatable deployments, which you can transfer to any region or cloud provider, that become the first step in your new disaster recovery plan.
- Consistent application of essential traffic policies—again, you must implement them in Git, not in your gateway provider’s web console or admin API.
Your line of questioning then becomes: Does your API gateway even let you do APIOps? If yes, the conversation quickly devolves into: How do you actually get the process right? Even with the right groove right in front of you, it’s easy to lead your team astray.
Case No. 1: Pure developer freedom
The younger the company, the more likely you are to have picked up an API gateway provider that allows for some degree of APIOps, and the more likely you are to let everyone create, configure, and deploy APIs with abandon. You need to drive toward that MVP or pivot before you burn through your cash, so it doesn’t matter that every API is unique.
Different providers. Different authentication policies. Different repositories. Different branch protections. Different disaster plans. Different ideas of what “quality,” “security,” and “availability” mean.
You can move fast, but it sure is chaotic.
Case No.2: Centralized DevOps/platform management
Larger and older companies are more likely to have dedicated teams who “own” the APIOps process. They maintain the quality of the production environment by establishing guardrails that dictate how developers should design and deploy APIs.
You’re grateful for their high standards and not having to worry so much about the operational end of the API lifecycle, but you also feel the pain of pushing all your hard work through them.
Your APIs might be perfectly stable, but the congestion slows you down.
Find the common problem!
You might think APIOps, as a methodology, is somehow flawed. If it can’t help developers get back into their groove, what’s the point? The failure mode here isn’t APIOps, but rather how most API gateways handle ingress and the global delivery of your APIs. In other words: They don’t.
Deployed API gateways operate from a single point of failure and require sophisticated Ops handiwork, and cloud API gateways lock you into specific cloud providers and don’t offer nearly as much deep customization. In either case, the networking and operational task of connecting multiple API gateways to your infrastructure and a global delivery network is far from your core competency. You’re still on the hook for high availability and failover processes. You’re still waiting on the NetOps team to give you the green light on an API you wrapped up two weeks ago.
APIOps makes the early phases of the lifecycle developer-friendly, but you still need developer-friendly ingress at the very end of the line.
Building with ngrok’s production-grade API gateway and unified ingress
We built ngrok’s API gateway to be both flexible and developer-defined, which means it’s ready for APIOps workflows that work in the same groove you already know and love. Adopting APIOps gets quite straightforward once you have unified ingress from ngrok.
For example, you start by developing a new API in a single Git repository for your backend service, a Dockerfile to containerize said service, and a few IaC files in the form of Kubernetes manifests in YML.
Git-based foundation? ✅
Next, you provision a Kubernetes cluster—could be a minikube cluster on your local workstation for a proof of concept, or its production-grade counterpart in GKE. Use Helm to install ngrok Kubernetes Operator to take care of secure and flexible ingress, followed by a GitOps tool like Argo CD to tackle all the work around continuous deployment.
Automated and repeatable GitOps deployments using Git as your source of truth? ✅
Next, you add API gateway Traffic Policies to your existing IaC by layering new CRDs and referencing them throughout your HTTPRoutes, which the Kubernetes Operator uses to direct incoming traffic to your containerized backend API service. Traffic Policies execute on both inbound requests and outbound traffic, allowing you to quickly layer in JWT authentication, rate limiting, and plenty of other custom rules.
API gateway policies defined by YAML and version-controlled with Git? ✅
Finally, you can enable Argo CD’s auto syncing feature to automatically deploy every merged commit, whether that’s a bugfix on your backend service or a new authentication method to protect your public API from abuse.
Full-on APIOps? ✅
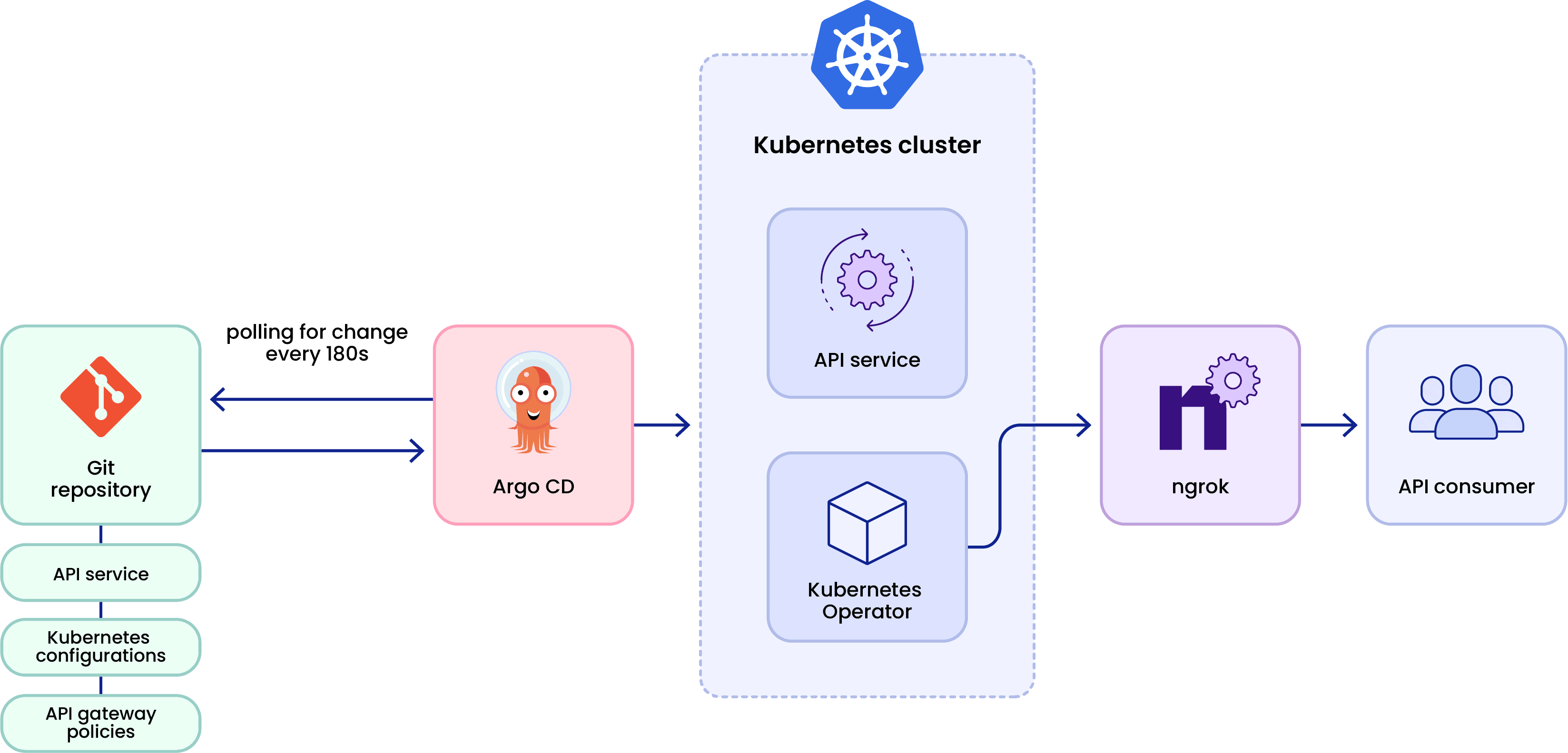
ngrok helps you avoid the problematic cases mentioned above through unified ingress. No more worrying about networking infrastructure or TLS certificate generation. No more pondering over a global delivery network, high availability, or geo-aware failover. Developers work efficiently on the convenience API gateway interface, and operators—when they are indeed in the picture—to green-light new deployments faster than before.
No chaos. No congestion. Just one smooth groove.
Check out our how-to guide for a full walkthrough of the technical setup to bring APIOps to your next API project with ngrok.
In the end, your APIOps workflow on ngrok comes with some extra benefits, too:
- Environmental independence, so that a single Git repository deploys the exact same on your local machine, in a staging environment spun up by your CI/CD process, or in production.
- Global acceleration and load balancing to minimize latency no matter where your API consumers are requesting from and enable automatic recoveries from failures to keep your APIs online.
- More developer autonomy to control API policies like rate limiting and request/response manipulation, plus deeper governance guardrails, without relying entirely on operational peers.
- Built-in DDoS protection that blocks both malicious attacks and misconfigurations from overloading your upstream deployment.
- Observability features like the Traffic Inspector to capture and even replay specific requests directly through your ngrok dashboard.
What’s next?
Your new API development groove now includes ngrok—if you haven’t yet, sign up now to start defining your API gateway through Git and IaC, not obscure admin API calls.
Once you have an account, check out not just the how-to guide, but all our other resources on how ngrok’s developer-defined API gateway works alongside Kubernetes APIOps-ready deployments.
- How-to guide: Deploy a production API and gateway with APIOps using Argo CD and ngrok
- ngrok blog: Traffic Policy support for the Kubernetes Gateway API
- Docs: Kubernetes Operator user guide — Traffic Policy gateway composition
Once you’ve tried our how-to guide or bravely implemented the core APIOps concepts in your own infrastructure, we’d love to hear from you in our new ngrok Community Repo, the best place for all discussions around ngrok, including bug reports and product feedback.

Joel Hans is a Senior Developer Educator at ngrok. He has plenty of strong thoughts about documentation, developer education, developer marketing, and more.