The challenges organizations face when managing access control and authorization in cloud-native environments continue to grow in complexity. Organizations scaling their Kubernetes deployments, for example, work to balance their security requirements, operational flexibility, and policy manageability. Cedar, an open-source policy language and evaluation engine, offers a fresh perspective for addressing these challenges.
What is Cedar?
Cedar is a policy language designed for modern authorization needs. Though traditional role-based access control (RBAC) serves as a foundation for many organizations and applications, Cedar extends beyond simple role assignments to provide more nuanced and powerful policy controls.
Cedar is both human-readable and machine-analyzable. Its policy structure supports quick retrieval, real-time evaluation with bounded latency, and suitability for large-scale deployments. Automated reasoning tools use Cedar to analyze and optimize policies, helping administrators prove their security model behaves as intended.
Cedar for Kubernetes: Bridging the Gap
Traditionally, Kubernetes administrators have had to manage different policy frameworks and tools for different types of controls—one set of tools for authorization, another for admission control, and possibly others for additional security requirements. Numerous other challenges stem from Kubernetes RBAC’s existing limitations: RBAC is allow-only and does not support denials, it does not support attribute-based access or conditions, and it does not support any form of glob matching for selection.
Cedar’s integration with Kubernetes overcomes these challenges. Administrators can write both authorization and admission policies by using the same language and framework. This significantly reduces cognitive overhead and the risk of security gaps that can occur when managing multiple policy systems. Additionally, Cedar supports rich condition operators that allow fine-grained permissions on specific resources.
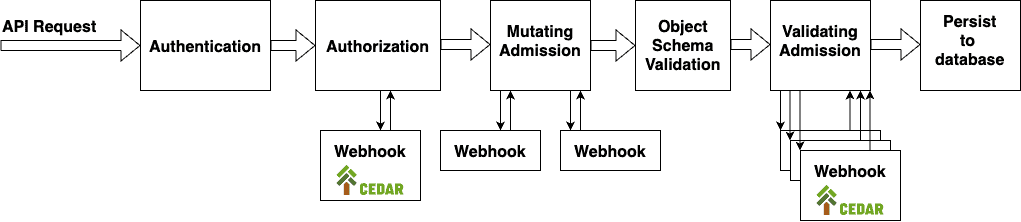
Cedar for Kubernetes uses a combination of pluggable authorization and admission validation webhooks to enforce access controls within a cluster.
As shown in the following diagram, Cedar can be used to validate multiple extension points in the Kubernetes API, where traditionally separate policy formats are used with authorization and admission validation to enforce access controls in Kubernetes.
Key Features and Benefits of Cedar for Kubernetes
Cedar for Kubernetes provides these key features and benefits:
- Label-based access controls and attribute-based rules that allow policy authors to construct policies that enforce new boundaries in a Kubernetes cluster.
- Custom resource definitions (CRDs) for storing Cedar policies directly in Kubernetes clusters. Users can use CRDs to define permissions as Kubernetes resources in a cluster.
- Compatibility with existing RBAC configurations through a converter. Users can easily migrate and customize existing policies without manual effort.
- Support for Kubernetes impersonation authorization so that users can easily author correct impersonation policies.
- Automatic schema generation for Kubernetes built-in types and CRDs so that user-authored policies can be validated for correctness.
- Unified policy management for both authorization and admission controls to reduce cognitive load on policy authors.
Cedar for Kubernetes excels in its ability to maintain compatibility with existing RBAC configurations while providing sophisticated policy controls. This means organizations can gradually adopt Cedar without disrupting their current security posture.
Real-World Applications
Consider the common scenario of ensuring that all pods in a Kubernetes cluster have billing and owner labels set. With traditional policy frameworks, this might require separate tools and languages for enforcement. With Cedar, administrators can express both the permission to list, and create pods and the requirements for labels in the same policy file, making it easier for them to review and maintain security controls.
Another common authorization need is to enable a security or observability pod the ability to list or modify other pods that are assigned to the same node. This is not possible today with Kubernetes RBAC, and operators often resort to granting an application more permissions than required, including permissions that can affect pods on other nodes. Cedar makes expressing this kind of attribute-based access simple and concise, enabling administrators to enforce tightly constrained least-privilege permissions.
Looking Forward
The cloud-native ecosystem continues to evolve, and with it, approaches to security and policy management must adapt. Cedar represents a step forward in this evolution, offering a new approach to policy management that aligns well with the cloud-native principles of scalability and automation.
Organizations interested in exploring Cedar with Kubernetes can begin by using tools such as kind in development environments. The Cedar for Kubernetes project is open source and welcomes community involvement. This means you can try Cedar for free without any cloud dependencies.
Conclusion
As Kubernetes deployments grow in complexity, the need for more sophisticated yet manageable policy controls is increasingly important. Cedar’s approach to policy management—combining human-readable policies with machine-analyzable capabilities—represents a promising direction for the future of cloud-native security.
Cedar for Kubernetes’ integration and unification of authorization and admission controls under a single policy language addresses a need in Kubernetes security management. Though this integration continues to mature, Cedar’s core principles of unification, analyzability, and scalability align well with the challenges facing modern cloud-native deployments.
Cedar offers a path toward sophisticated, maintainable, and verifiable policy management for organizations looking to evolve their Kubernetes security strategies. As the Cedar for Kubernetes project continues to develop and gather community feedback, it has the potential to significantly improve how we approach authorization and policy management in cloud-native environments.
To read more about Cedar for Kubernetes, try it out locally, or contribute to it, see the Cedar for Kubernetes GitHub repository.
If you are attending KubeCon + CloudNativeCon Europe 2025, then meet with us at the AWS Booth S300 to see demos on AWS open source projects.